PicoCTF packer writeup
Using the strings command reveals that UPX was used.
UPX!<
P/PI
}_PzH
F^lx/
Bf/P
@/ j
ME=n
[GSd2
t>d4
8%'u
{PXP
0 !
:
Note: UPX stands for Ultimate Packer for eXecutables. It’s a runtime executable packer.
Using upx -d out will decompress the program.
Then use something like gdb, ida or ghidra to get the flag.
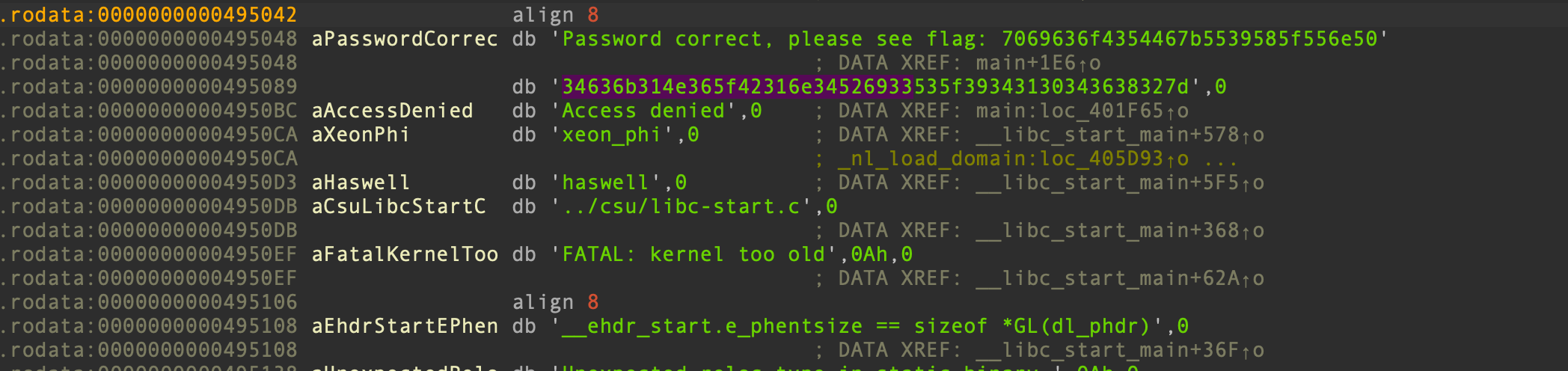
The password is in hex convert it to ascii to get the flag. 7069636f4354467b5539585f556e5034636b314e365f42316e34526933535f39343130343638327d
picoCTF{U9X_UnP4ck1N6_B1n4Ri3S_94104682}
Resources
- https://play.picoctf.org/ - PicoCTF
- https://play.picoctf.org/ - GEF